Fraud activity is a growing threat to businesses, and it’s essential to understand the methods used by criminals. Most commonly, fraud is done through identity theft. Worst of all, users often let them do this because they don't know how the scam works. Impostors obtain personal information, such as Social Security Numbers or driver's license numbers, which can be used to open accounts or apply for credit in someone else’s name. Another method of fraud is synthetic identity fraud. This involves combining existent and false information to create a new identity. Once the new identity is made, the criminal uses it to apply for credit or open accounts.
In such situations, it is extremely difficult for the user to recognize fraudsters independently. Still, understanding fraud strategies can help companies protect themselves from such dangers and strengthen the protection of their users' data. Businesses may reduce their risk of becoming fraud victims by making efforts to authenticate identities and detecting the warning indications of fraud.
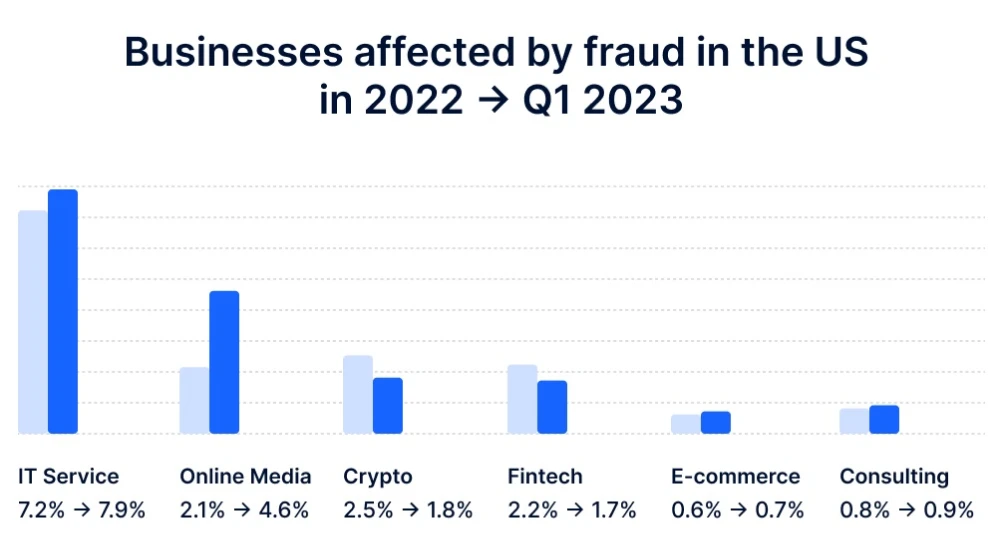
If you think there are very few such situations, because the industry is already quite developed and it ensures complete data confidentiality, then you are mistaken. Every day, as anti-fraud software is invented, the emergence of new fraudulence is also increasing.
So how to overcome it? Let's figure it out together with Mobupps in this article.
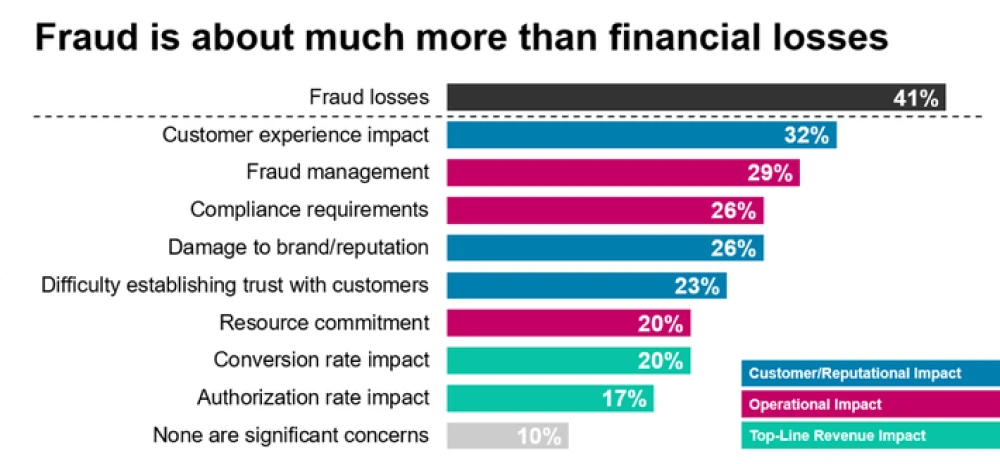
In the modern digital era, the issue of application fraud is a grave concern, underscoring the necessity of its timely detection. Application fraud arises when individuals utilize purloined or fabricated details to seek loans, credit cards, jobs, or various services. This kind of fraudulent activity can give rise to a range of complications, including identity theft and monetary loss. Furthermore, the application fraud identification is crucial due to its potential to spawn other forms of deceit, such as money laundering and support for terrorist activities.
To effectively identify application fraud, businesses must establish appropriate protocols. These protocols encompass procedures like verifying the authenticity of applicants' identities, conducting thorough background assessments, and validating the precision of the furnished information. Instituting these proper procedures not only aids in fraudulent activity detection but also acts as a shield for businesses against adverse financial outcomes and damage to reputation.
However, detecting application fraud is no small feat. It requires a combination of sophisticated technology and skilled investigators. Fortunately, Mobupps knows the solution and provides best-in-class proactive fraud prevention technology - MAFO.
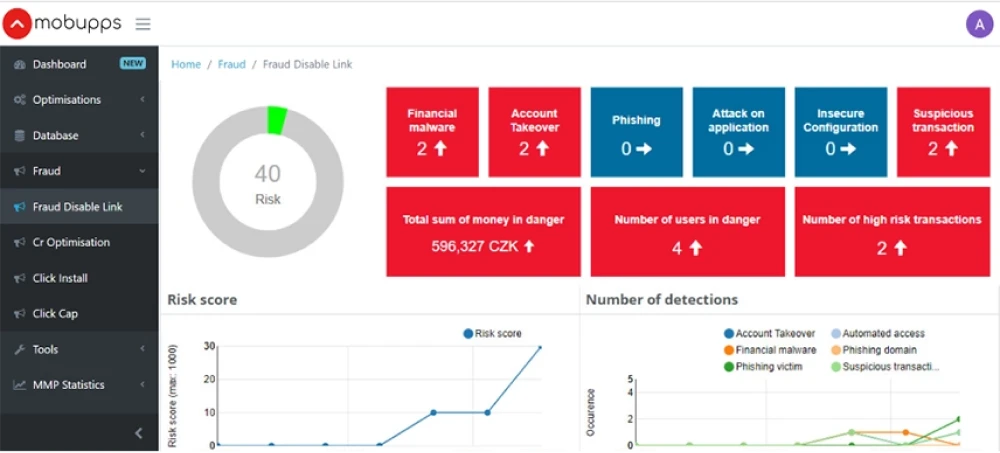
MAFO is an automated technology that transparently generates the user base, expands the audience, and measures the overall ROI with an almost completed fraud-blocking rate. MAFO can block as much as 98.2% of all fraud clicks. 3-layered anti-fraud protection and verification brings the highest lead quality and excludes every fraud attempt.
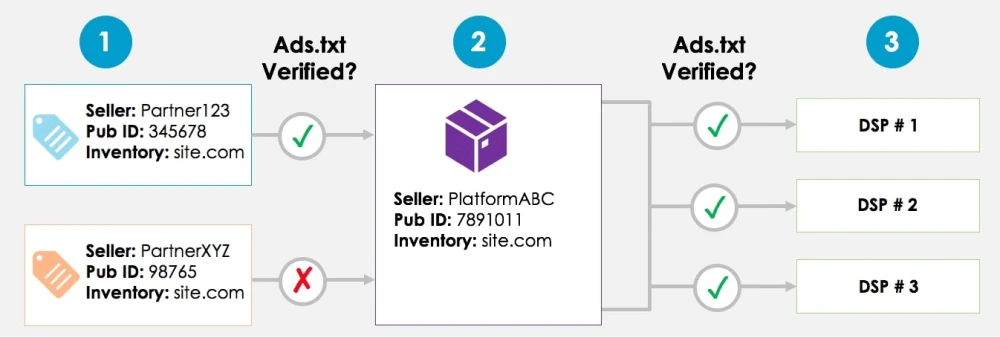
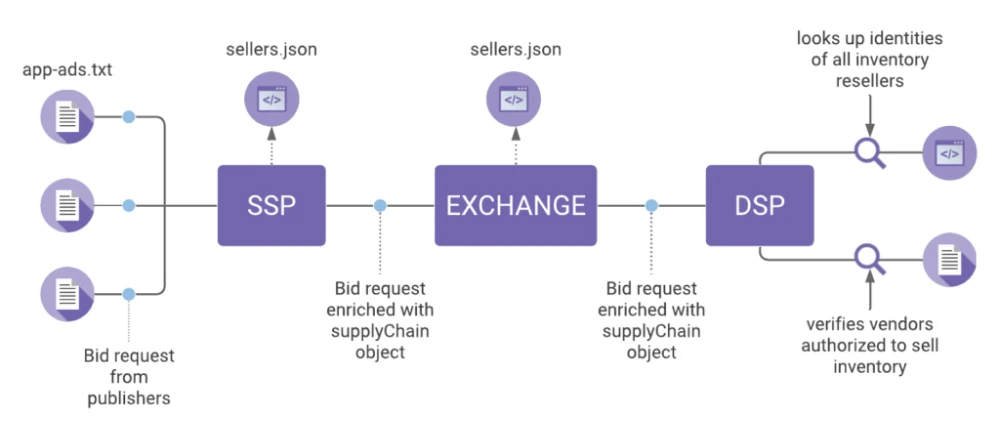
Ads.txt compliant with more than 60% coverage. Ads.txt is a global market project under the auspices of the IAB, designed to protect clients' money from fraud traffic costs. Ads.txt helps the client to verify the traffic purchase channel. In the ads.txt file, the publisher specifies all authorized sellers of its traffic. During the placement of an advertising campaign, the client can compare the seller's ID with the positions in ads.txt on the site. If the seller is authorized, the purchase is safe. If not, the purchase is at the risk and peril of the client.
Sellers.json is a bit like the SSP’s version of the publisher’s ads.txt file. Ad tech vendors buying and selling impressions on the open exchange typically work with an enormous array of intermediary resellers, all of which work with other resellers. That complex web of players involved in the sale of every impression makes it virtually impossible to keep track of who is reselling whose inventory, and whether they’re authorized to by the vendor that has a direct relationship with the publisher.
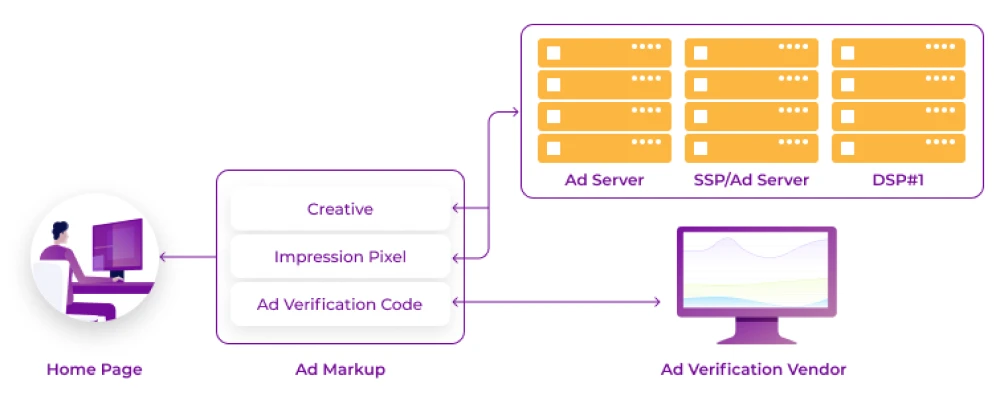
Monitoring Pixalate Pre and Post-bid IVT is the best solution that prevents invalid traffic (IVT) and reduces brand risk while growing your ad ROI with the pre-bid GIVT and SIVT blocking across Connected TV (CTV), Mobile Apps, and Websites coming from 8+ million apps, 80 million domains, and 300+ million OTT devices.

Ad verification by GeoEdge can pre-approve all ad creatives on our platform. We and our publishers have peace of mind, knowing every ad campaign that goes live has been evaluated for safety and compliance.
Besides that, MAFO's audience profiling technology allows users to predict user intent by leveraging historical data and pre-selecting ideal campaign placements. It is also fully transparent in all traffic sources at a granular level from integration with data received from various sources (tracking systems, MMP, anti-fraud systems)
Application fraud is a serious issue that can have far-reaching consequences. By detecting and preventing it, businesses can protect themselves and their customers from financial losses and identity theft. At Mobupps, we fight against fraud daily and are professionals in this field. Our knowledge and valuable experience in the fight against fraud can significantly reduce the severity of fraudulent attacks on your software products or services. Contact Mobupps to get rid of army bots, emulators, click spammers, and scammers.
Fraud activity is a growing threat to businesses, and it’s essential to understand the methods used by criminals. Most commonly, fraud is done through identity theft. Worst of all, users often let them do this because they don't know how the scam works. Impostors obtain personal information, such as Social Security Numbers or driver's license numbers, which can be used to open accounts or apply for credit in someone else’s name. Another method of fraud is synthetic identity fraud. This involves combining existent and false information to create a new identity. Once the new identity is made, the criminal uses it to apply for credit or open accounts.
In such situations, it is extremely difficult for the user to recognize fraudsters independently. Still, understanding fraud strategies can help companies protect themselves from such dangers and strengthen the protection of their users' data. Businesses may reduce their risk of becoming fraud victims by making efforts to authenticate identities and detecting the warning indications of fraud.
If you think there are very few such situations, because the industry is already quite developed and it ensures complete data confidentiality, then you are mistaken. Every day, as anti-fraud software is invented, the emergence of new fraudulence is also increasing.

So how to overcome it? Let's figure it out together with Mobupps in this article.
In the modern digital era, the issue of application fraud is a grave concern, underscoring the necessity of its timely detection. Application fraud arises when individuals utilize purloined or fabricated details to seek loans, credit cards, jobs, or various services. This kind of fraudulent activity can give rise to a range of complications, including identity theft and monetary loss. Furthermore, the application fraud identification is crucial due to its potential to spawn other forms of deceit, such as money laundering and support for terrorist activities.
To effectively identify application fraud, businesses must establish appropriate protocols. These protocols encompass procedures like verifying the authenticity of applicants' identities, conducting thorough background assessments, and validating the precision of the furnished information. Instituting these proper procedures not only aids in fraudulent activity detection but also acts as a shield for businesses against adverse financial outcomes and damage to reputation.

However, detecting application fraud is no small feat. It requires a combination of sophisticated technology and skilled investigators. Fortunately, Mobupps knows the solution and provides best-in-class proactive fraud prevention technology - MAFO.
MAFO is an automated technology that transparently generates the user base, expands the audience, and measures the overall ROI with an almost completed fraud-blocking rate. MAFO can block as much as 98.2% of all fraud clicks. 3-layered anti-fraud protection and verification brings the highest lead quality and excludes every fraud attempt.

Ads.txt compliant with more than 60% coverage. Ads.txt is a global market project under the auspices of the IAB, designed to protect clients' money from fraud traffic costs. Ads.txt helps the client to verify the traffic purchase channel. In the ads.txt file, the publisher specifies all authorized sellers of its traffic. During the placement of an advertising campaign, the client can compare the seller's ID with the positions in ads.txt on the site. If the seller is authorized, the purchase is safe. If not, the purchase is at the risk and peril of the client.

Sellers.json is a bit like the SSP’s version of the publisher’s ads.txt file. Ad tech vendors buying and selling impressions on the open exchange typically work with an enormous array of intermediary resellers, all of which work with other resellers. That complex web of players involved in the sale of every impression makes it virtually impossible to keep track of who is reselling whose inventory, and whether they’re authorized to by the vendor that has a direct relationship with the publisher.

Monitoring Pixalate Pre and Post-bid IVT is the best solution that prevents invalid traffic (IVT) and reduces brand risk while growing your ad ROI with the pre-bid GIVT and SIVT blocking across Connected TV (CTV), Mobile Apps, and Websites coming from 8+ million apps, 80 million domains, and 300+ million OTT devices.

Ad verification by GeoEdge can pre-approve all ad creatives on our platform. We and our publishers have peace of mind, knowing every ad campaign that goes live has been evaluated for safety and compliance.

Besides that, MAFO's audience profiling technology allows users to predict user intent by leveraging historical data and pre-selecting ideal campaign placements. It is also fully transparent in all traffic sources at a granular level from integration with data received from various sources (tracking systems, MMP, anti-fraud systems)
Application fraud is a serious issue that can have far-reaching consequences. By detecting and preventing it, businesses can protect themselves and their customers from financial losses and identity theft. At Mobupps, we fight against fraud daily and are professionals in this field. Our knowledge and valuable experience in the fight against fraud can significantly reduce the severity of fraudulent attacks on your software products or services. Contact Mobupps to get rid of army bots, emulators, click spammers, and scammers.

